Today data security during financial transactions is super important and critical. The protection of sensitive user data should be a major priority for developers working on applications that use financial or personal information of the clients.
These days, many apps are accessed through multiple devices including desktops, laptops, mobile phones and tablets. Both web apps, and native apps can use web APIs for accessing data and providing services. This article addresses the topic of ensuring client security of a web API during the development phase. I will share my experience with using JSON web tokens (JWT) to ensure security of a representational state transfer (REST) web API.
There are a two simpler alternatives to JWT that I will briefly mention first:
-
Basic authentication:
This method is very easy to implement. A username and password is passed and validated in a database to identify legitimate users. Since the username and password are sent as plain text, every request is very susceptible to cross-site request forgery (CSRF). The security can be improved somewhat by passing the details in the headers section of the web API instead of the URL, nevertheless this method is not very secure as it does not involve any encryption.
-
API keys:
This technique is used to overcome the drawbacks of basic authentication. In this method, a unique key is assigned every time the user signs in indicating that the user is known. A user can use the same key to re-enter the system. The security issue with this method is that the key can easily be picked up during network transmission. Often, the key is passed as a query string in the URL, making it easier for someone to compromise the security of the web API.
JWT avoids the security flaws of the two simpler methods, by providing a bearer token authentication of the Web API. With this method, the user name and password validates, whether, the user exists in the system. Information about the validated user like name, email address and UserID can be fetched. These items are included in the ‘claim’. Claims are pieces of information about a user that have been packaged and signed into security tokens.
A JWT token consists of three parts, the header, the payload and the signature.
Header – Contains the type of token and signing algorithm used
Payload – Contains the issuer of the claim, the subject of the claim and the audience, which refers to the intended recipient of the claim. Other information can also be included, such as an expiry time of the token, or additional user information.
Signature –Contains the encoded header, encoded payload and a secret key
Implementation
To give you more details about JWT implementation, I’ll be going through the steps I took to implement JWT in my web API. First I created a web API project in .Net core 2.2. Next I installed two packages via npm of visual studio, using the following commands:
- Install-Package System.IdentityModel.Tokens.Jwt -Version 5.6.0
- Install-Package Microsoft.AspNetCore.Authentication.JwtBearer -Version 3.1.0
In the appsetting.json file, I added my JWT keys including the secret key, issuer, subject and audience as follows:
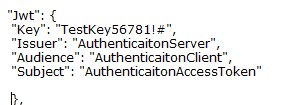
Next, I registered a JWT authentication schema by using the "AddAuthentication" method and specifying JwtBearerDefaults.AuthenticationScheme. in the ConfigureServices section of the start-up class.

I also added app.UseAuthentication() in the configure method of the startup class.

Next, I created a token controller in the web API. This token controller action GetApiToken took the two input parameters: Username and Password, and validated these details against the database. Once the user is validated, I generated a token using the secret key, claims information and signing credentials.

The generated token was then stored as an item in sessionStorage.
For all my web API requests, I used the following key in the header section of each Ajax web API call request.

Finally, I applied the [Authorize] attribute to my controller to which I was calling the web API.

These were all the steps I required to implement JWT authentication in my Web API. The tokens are encrypted, so they are difficult to tamper with. They expire at specific intervals and are cryptographically signed using a cryptographic algorithm.

The final implementation step is to remove the generated token item which was stored in sessionStorage when a user logs out of the system.

MetaSys has extensive expertise in building secure web APIs for web applications. Our team has experience in building custom software solutions for clients across different industry verticals. Please feel free to contact us if you are in need of a partner to build a secure web API. For more info, visit our website: https://www.metasyssoftware.com/dot-net.